Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Report
Lorem ipsum dolor sit amet, consectetuer adip
Download this guide to learn:

Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt

Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam.

Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr

Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam.
Register to attend
We will send you news and updates by email. You may opt out any time. We’ll store your information in accordance with our privacy policy.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Related resources

Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet

Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet

Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet
Sessions
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
I'm a header that can be moved anywhere
I'm a header that can be moved anywhere
I'm some paragraph text to go with the header

Download the full report
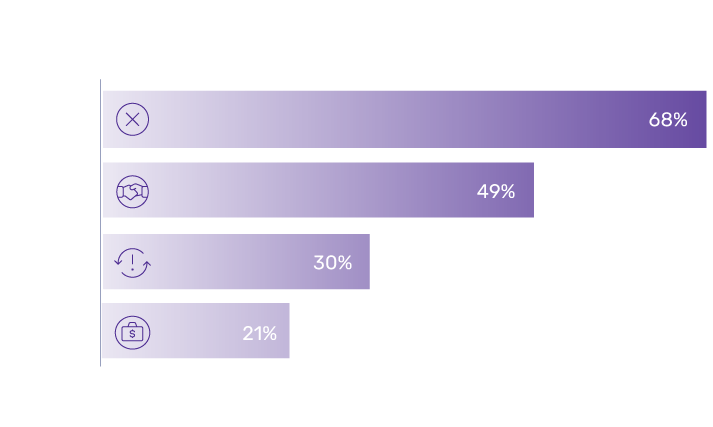
100%
of organizations suffered negative impacts when information barriers were breached
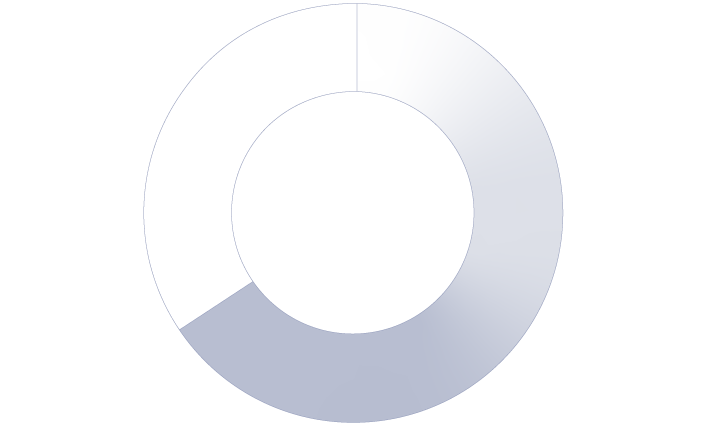
66%
of organizations enforcing information barriers in Microsoft 365 have had them breached
85%
of employees say they rely on email more than ever
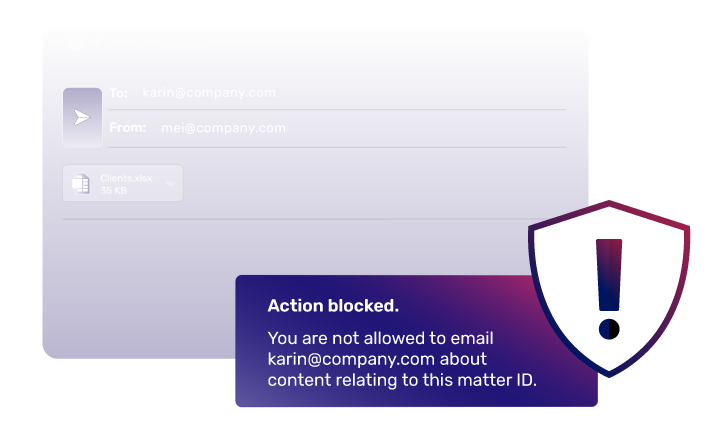
Independent research reveals the impact of breached information barriers
Organizations can only take back control using intelligent email DLP.

Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.

Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.

Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.

Independent research reveals the impact of breached information barriers
Organizations can only take back control using intelligent email DLP.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
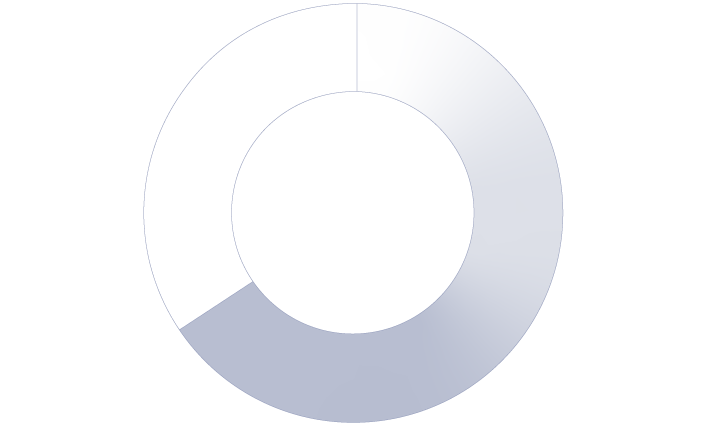
Employees rely on email now more than ever
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.

Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.

Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
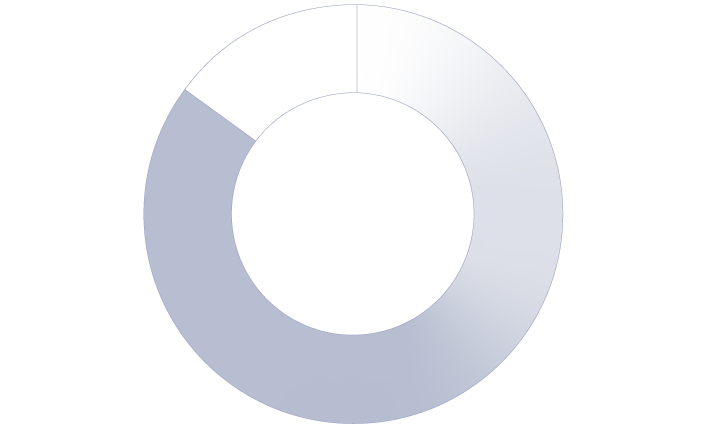
66% of organizations that enforced information barriers on email in Microsoft 365 say they've been breached
Independent research reveals the impacts following an internal breach of information barriers
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
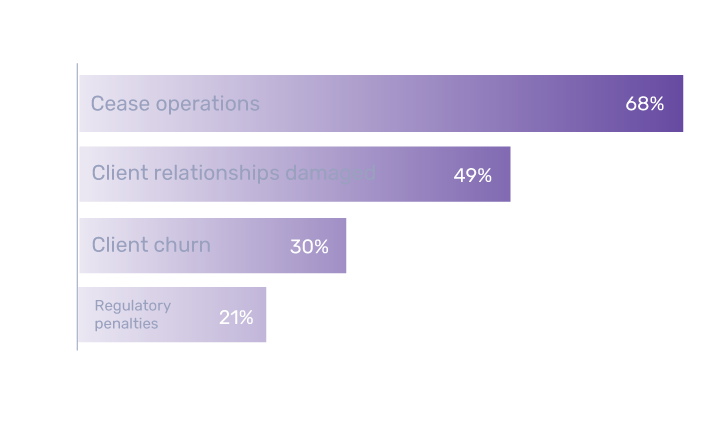
Accusamus molestiae corporis delectus rerum mollitia?
Sed, officia. Minima mollitia optio esse est blanditiis ex possimus provident.

92%
implement a defense-in-depth strategy
49%
feel their security stack is too complex

"Ultimately, firms deploying intelligent email DLP can enhance their competitive edge, operate with great efficiency, and preserve client relations, all positively influencing revenue generation and retention.”


Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua.
John Smith, Head of Security at Browns Ltd.
92%
implement a defense-in-depth strategy
49%
feel their security stack is too complex

Download your free report

Download your free report


© 2007-2024. All rights reserved. Egress Software Technologies Ltd.