Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Bi-directional technology integration
Personalize KnowBe4 training using real threat data
BI-DIRECTIONAL TECHNOLOGY INTEGRATION
Personalize KnowBe4 training using real threat data
Learn more about the integration from one of our experts
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.

Lorem ...
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amit.
Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr. Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet, consetetur sadipscing elitr.
Related resources

Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet

Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet

Sed diam voluptua. At vero eos et accusam et justo duo dolores et Lorem ipsum dolor sit amet
Sessions
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
Speakers

Tony Pepper
CEO, Egress

Chris Novak
Cybersecurity Advisor, The White House

Perry Carpenter
Chief Evangelist, KnowBe4
The Mind’s Lie: How to respond to employees’ thoughts and actions being hacked
We’re all wired to deceive and be deceived. Join Perry Carpenter and Jack Chapman for an engaging exploration into the dark world of deception and the current threats people face.
After laying the groundwork on the art and science behind why people fall victim to social engineering, Perry and Jack will walk through practical examples of how cybercriminals exploit our decision-making processes and provide insight into the ways organizations can respond through a combination of technology and education.
I'm a header that can be moved anywhere
See how Egress tailors training in KnowBe4
Request a personalized demo
Download the full report
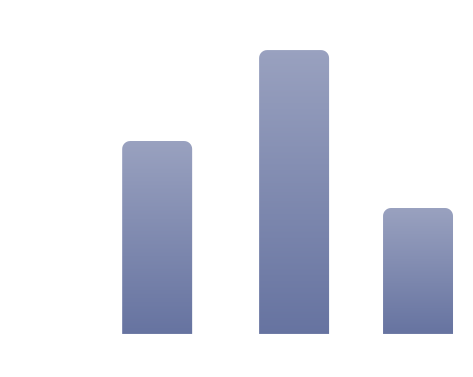
92%
implement a defense-in-depth strategy
69%
have between 11-30+ security products
49%
feel their security stack is too complex
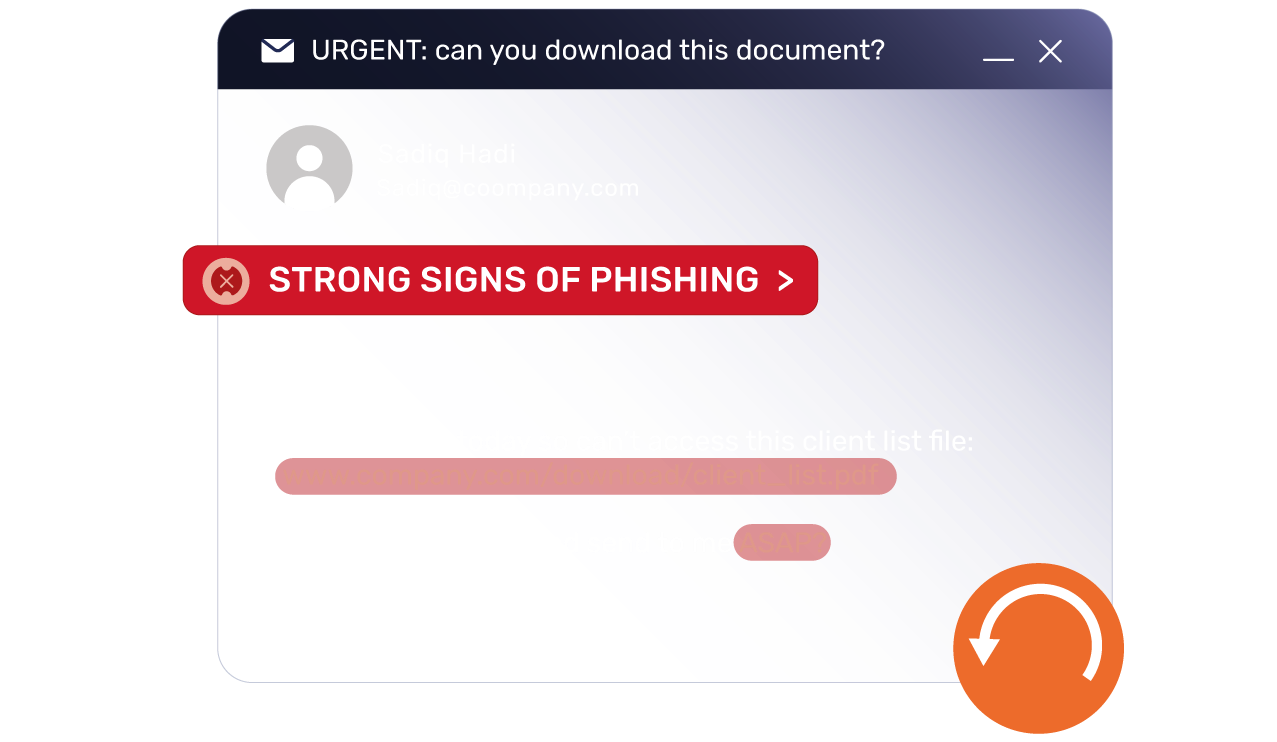
Auto-enrol users in KnowBe4 training modules – without clicking a button!
Live threat intelligence and Egress product telemetry is used to populate KnowBE4 Smart Groups to deliver fully automated behavioral-based training.
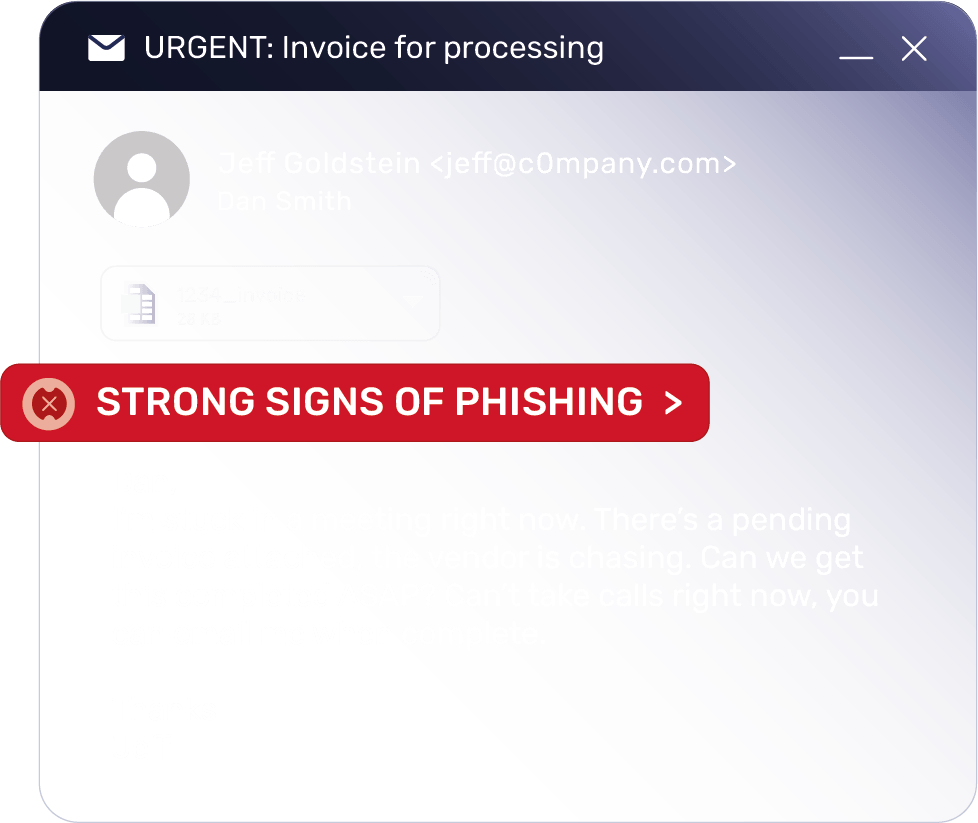
Dynamically deliver threat-based phishing simulations
Prepare users for real-world threats, assess security awareness, and identify risks by tailoring phishing simulation campaigns based on the threats each individual faces.
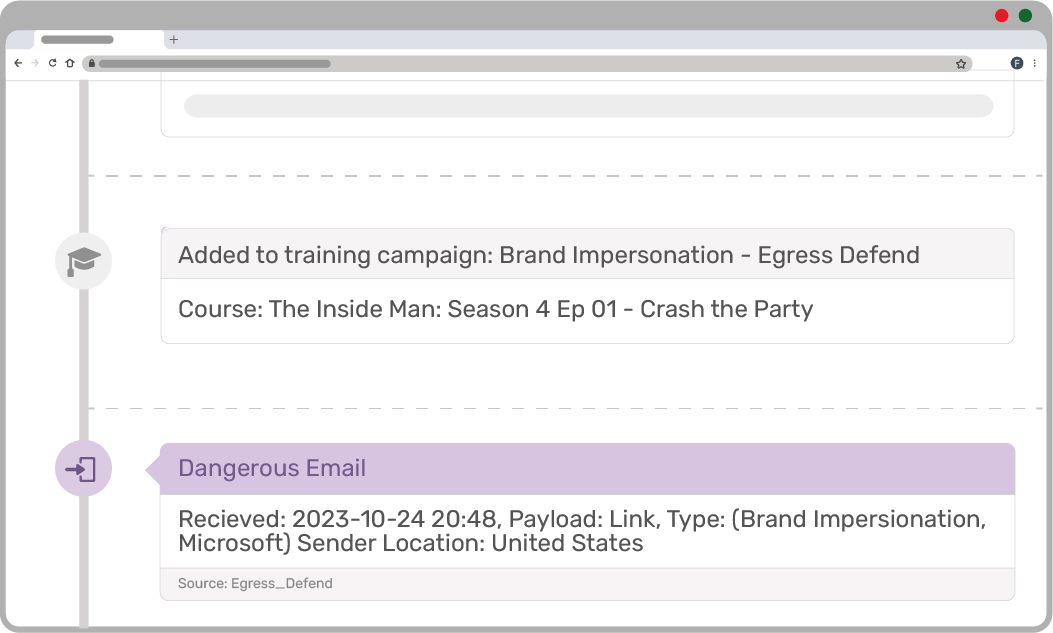
Enhance intelligence in the KMSAT platform
Egress' risk intelligence feeds into KnowBe4 KMSAT for event timeline visualization, enabling you to pinpoint areas of risk, analyze the impact of training, and demonstrate ROI.

Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.

Lorem ipsum dolor sit amet consectetur adipisicing elit. Eveniet quibusdam quis sit.

Minima mollitia optio esse est blanditiis ex possimus provident officia, enim libero quo sapiente quod porro.

Auto-enrol users in KnowBe4 training modules – without clicking a button!
Live threat intelligence and Egress product telemetry is used to populate KnowBE4 Smart Groups to deliver fully automated behavioral-based training.

Dynamically deliver threat-based phishing simulations
Prepare users for real-world threats, assess security awareness, and identify risks by tailoring phishing simulation campaigns based on the threats each individual faces.

Enhance intelligence in the KMSAT platform
Egress' risk intelligence feeds into KnowBe4 KMSAT for event timeline visualization, enabling you to pinpoint areas of risk, analyze the impact of training, and demonstrate ROI.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.

Earum enim voluptatum animi quisquam voluptates hic aliquid necessitatibus magni fugit rerum

Numquam quo tenetur dicta quibusdam officiis. Labore aliquam ducimus obcaecati
Watch a 2.5 minute overview of the KnowBe4 and Egress integration
Take 2.5 minutes to see Egress Head of Innovation James Sheldrake demonstrate how you can enhance KnowBe4 training and assessments.
Watch a 2.5 minute overview of the KnowBe4 and Egress integration
Take 2.5 minutes to see Egress Head of Innovation James Sheldrake demonstrate how you can enhance KnowBe4 training and assessments.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Out of 800 IT leaders...
Defense-in-depth is a popular strategy. Yet despite organizations constantly adding more layers to their security stacks, they remain vulnerable to inbound attacks and outbound breaches.
This report explores the drawbacks of introducing too many vendors and security technologies into your business, and why streamlining around one or several vendor suites can improve overall security.
Accusamus molestiae corporis delectus rerum mollitia?
Sed, officia. Minima mollitia optio esse est blanditiis ex possimus provident.

92%
implement a defense-in-depth strategy
49%
feel their security stack is too complex

Our partnership with Egress enables our customers to deliver individualized security coaching that drives behavioral change and reduces overall risk.
Stu Sjouwerman, CEO, KnowBe4


This is not just another product dashboard! By gathering data from multiple sources, including our SAT data from KnowBe4, Egress allows us to shine a spotlight on areas of risk we'd not previously considered.
Matt Nears, VP of Global IT Security, Crawford and Company
92%
implement a defense-in-depth strategy
49%
feel their security stack is too complex




© 2007-2024. All rights reserved. Egress Software Technologies Ltd.